松下達之研究室(情報セキュリティ研究室)

安全・安心な情報システムを支える情報セキュリティ技術を研究しています。デジタルデータを守るためには、他の人に見られないようにすること(機密性)が重要です。本研究室では、サイバー攻撃から防御し、データの機密性を保つための暗号プロトコルの研究を行っています。計算量的な仮定に基づいた数学的な証明や計算機シミュレーションを用いて、暗号プロトコルの安全性を評価します。安全で信頼性の高い情報社会の実現をめざしています。
| 教員名・所属 | 松下達之 / データサイエンス学科 |
|---|---|
| 専門分野 | 情報暗号化技術 |
| 研究テーマ |
|
| 研究キーワード | 代理再暗号化、非転移性、再暗号化の非偽造性、対共謀攻撃 |
| 教員紹介URL | https://www3.med.teikyo-u.ac.jp/profile/ja.95dd71ee3282c480.html |
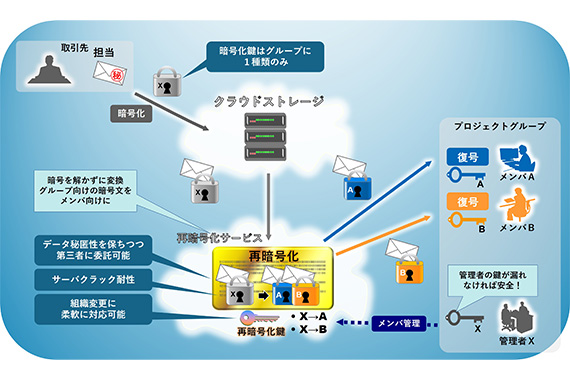
暗号を解かずに、特定のグループメンバの鍵で復号可能な暗号化データに変換する技術です。クラウドストレージにおいて暗号化したままデータを共有する仕組みに応用し、公開鍵暗号の技術を応用して実現します。
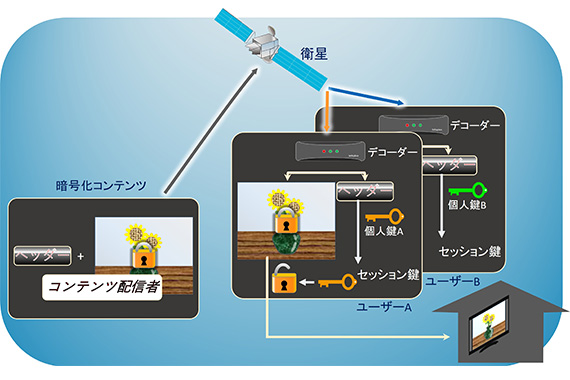
映画などのデジタルコンテンツ配信サービスにおいて「ただ見」を抑止する技術です。不正に作成された海賊版デコーダ(暗号化コンテンツを復号する機器やソフトウェア)からその海賊版デコーダの作成に加担した不正ユーザを特定します。
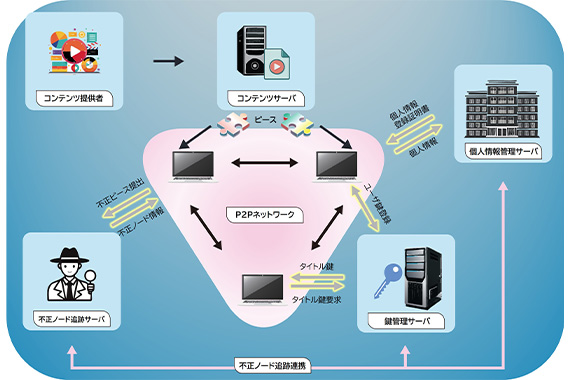
ピアツーピア(P2P)配信において、共通復号鍵が流出すると暗号化コンテンツがすべて復号可能となってしまう課題を解決します。課題を解決するために、計算機シミュレーションにより安全性や効率性を評価します。